#security
News | News Items
Elderly woman and her son killed at home in Hezbollah anti-tank missile attack | The Times of Israel
Barak Ayalon, 45, member of Kfar Yuval security team, killed alongside mother Miri Ayalon, 76, when projectile from Lebanon slams into northern town
Science & Technology | Technology
Now even the FBI is warning about your smart TV’s security | TechCrunch
If you just bought a smart TV on Black Friday or plan to buy one for Cyber Monday tomorrow, the FBI wants you to know a few things. Smart TVs are like regular television sets but with an internet connection. With the advent and growth of Netflix, Hulu and
News | News
Forming a U.S.-Led Coalition Against Iran with Brig. Gen. Amir Avivi - YouTube
As Iran moves closer to nuclear weapons capability and enriches uranium to just under the threshold for a bomb, the region faces increased threats and greate...
Advice & Self-Help | Advice & Self-Help
Cash Apps Can Be a Dangerous Way to Pay Rent — Here Are 5 Tips for Doing It Safely
Cash apps can be a dangerous way to pay rent. A simple mistake can make your rent payment disappear, according to a cybersecurity expert.
Science & Technology | Tech
Change this iPhone setting to thwart thieves who might steal your phone
iPhone thieves will try to enable Airplane Mode on the device - here’s how to block Control Center access right now.
Miscellaneous | Other Stories
If These Apps Are Still on Your Phone, Someone May Be Spying on You
Some of those apps you love and have come to rely on could be posing more of a danger than they're worth. Here's what you need to know.
Science & Technology | Technology
10 Tips to Have Secret Text Conversations on Your iPhone
While Apple works on its privacy features for text messages, you can use these tips and workarounds to have secret conversations on your iPhone.
Politics | Politics
Dem Sen. Warner says ‘Trump was right’ about banning China’s TikTok, warns parents against letting kids on app | Fox New
Sen. Mark Warner warned parents not to allow their kids to download TikTok, saying former President Donald Trump "was right" about the China-owned video app.
News | News
Patriot Truth News - Federal Data Quietly Reveals 100 Terror Suspects Caught At Southern Border
Newly published federal data reveals that close to a hundred individuals listed on the FBI terror watchlist have been apprehended at the Southern border in the last year, a record high and a huge uptick in recent months. The Customs and Border Protection
Science & Technology | Tech
Facebook warns 1 million users whose logins were stolen by scam mobile apps
402 malicious apps plagued Apple and Google’s stores.
Science & Technology | Tech
Apple warns of security flaw for iPhones, iPads and Macs that allows hackers to access devices
Apple said the vulnerability would allow a hacker to impersonate a device's owner and subsequently run any software in their name.
Science & Technology | Tech
FCC Commissioner urges Google and Apple to ban TikTok
Brendan Carr references reports that say Beijing-based employees have access to US TikTok user data..
Science & Technology | Technology
How Apple, Google, and Microsoft will kill passwords and phishing in one stroke | Ars Technica
You've heard for years that easier, more secure logins are imminent. That day is here.
Science & Technology | Tech
Some Top 100,000 Websites Collect Everything You Type—Before You Hit Submit
A surprising number of the top 100,000 websites effectively include keyloggers that covertly snag everything you type into a form.
Miscellaneous | Interesting Links
Google will now remove your phone number and other info from search results. Here's how to do it. - CBS News
To deter scammers and other bad actors, the search giant is now letting people remove personal contact information.
Science & Technology | Tech
3 Windows settings you can change to improve PC security
Here are three easy ways to improve PC security while also protecting your files and system information from bad actors.
Science & Technology | Tech
Apple just released a bunch of iPhone security updates, and wow
You should really update. Like, now.
Science & Technology | Tech
Miffed security researcher finds way to get Apple talking, drops three iOS vulnerabilities
Almost six months after reporting the first vulnerability to Apple, a security researcher has gone public to reopen lines of communication with Apple.
Science & Technology | Tech
A huge new hacking threat was just discovered
"You have the watches," goes a famous quote with different variations throughout history but most recently attributed to a captured Taliban commander, "but we have the time.
Science & Technology | Tech News
This site tells you if Google’s new ad tech is ‘spying’ on you
Google vowed a few weeks ago to stop allowing advertisers to track users online with third-party cookies, a move intended to improve user privacy. But Google also said at the time that it would introduce FLoC (or Federated Learning of Cohorts), a new tech
Science & Technology | Technology
Another 500 million accounts have leaked online, and LinkedIn’s in the hot seat - The Verge
An individual on a hacker forum is selling personal data they claim is scraped from 500 million LinkedIn profiles. LinkedIn says the data includes information from many places and not just the professional-focused social network.
Science & Technology | Tech
A new Android spyware masquerades as a ‘system update’ – TechCrunch
The malware can take complete control of a victim's device.
Science & Technology | Tech
Apple releases important iPhone, iPad, Mac and Watch security patches | TechCrunch
The tech giant said the security updates are "important" and are "recommended for all users."
Science & Technology | Technology
iOS 14.5 makes zero-click exploits ‘significantly harder’ according to security researchers
Amid the other new features in iOS 14.5, Apple has also implemented changes to how it secures the code running in iOS. As reported by Motherboard, the changes Apple has made behind the scenes here will make it harder for hackers to develop zero-click expl
Science & Technology | Tech News
Apple urges iPhone, iPad users to update operating system immediately after security flaws 'may have been actively exploited’
The security flaws impact the iPhone 6s and later, the iPad Air 2 and later, the iPad mini 4 and later, and the iPod touch (7th generation).
Science & Technology | Technology
iOS 14.4 update fixes iPhone security bugs, so it’s best to install it ASAP
Apple’s latest update for iPhones and iPads fixes major security flaws that the company says were potentially "actively exploited." Users should update to iOS 14.4 and iPadOS 14.4 as soon as they’re able.
Miscellaneous | Miscellaneous
Guy Who Reverse-Engineered TikTok Reveals The Scary Things He Learned, Advises People To Stay Away From It | Bored Panda
Facebook got itself into a sensitive data scandal when it did shady business with Cambridge Analytica, Instagram confirmed a security issue exposing user accounts and phone numbers, but these apps are basically online security havens compared to TikTok, a
Science & Technology | Tech
If you see your password on this list, change it as soon as possible – BGR
NordPass released a list of the 200 most common passwords of the year 2020 this week. Most of the passwords on this list also appeared on the 2019 list, and a vast majority of them can be cracked by a hacker in less than a second.
Science & Technology | Social Media
Crime ring stole thousands of Facebook passwords, then forgot to use a password - CNET
Exclusive: Researchers came across stolen user data in logs stored on a cloud server. It's offline now.
Miscellaneous | Interesting Links
5 Ways To Check For Hidden Cameras In Your Hotel Room Or Dressing Room
Privacy is perceived differently across the world. For example, in Germany, very few offices have open doors, while in America, this is quite common. However, nobody would be okay with secretly being watched, especially during private activities.
Science & Technology | Science & Technology
Zoom finally rolls out end-to-end encryption, but you have to enable it
Zoom made good on a promise to beef up the security of its video-conference calls. Here's how to enable end-to-end encryption.
Science & Technology | Technology
How to turn an old phone into a security camera for free - CNET
Here's how to give an old phone new life.
Science & Technology | Technology
The iOS 14 Privacy and Security Features You Should Know | WIRED
The latest update for your iPhone and iPad will make them safer than ever.
Politics | Politics
A bug in Joe Biden’s campaign app gave anyone access to millions of voter files
TechCrunch - Reporting on the business of technology, startups, venture capital funding, and Silicon Valley
News | International News
Hackers From China, Russia, Iran Targeting US Election: Microsoft
Microsoft said Thursday that hackers working for China, Russia, and Iran have recently ramped up their attacks, targeting ...
Science & Technology | Tech
Apple Accidentally Approved Malware to Run on MacOS | WIRED
The ubiquitous Shlayer adware has picked up a new trick, slipping past Cupertino's “notarization” defenses for the first time.
Science & Technology | Tech
Slack has fixed a major vulnerability in its desktop app
In the current age of remote working, more people are relying on team collaboration tools and Slack is one of the top services in the category. A security vulnerability in the service's desktop app, which is now fixed, could have…
Science & Technology | Israeli Innovation
Microsoft to buy Israeli cybersecurity startup CyberX
The U.S. software giant is expected to pay $165 million for the internet of things cybersecurity platform company
Science & Technology | Tech
How to Lock Down What Websites Can Access on Your Computer | WIRED
If you're not careful, websites can grab all kinds of permissions you don't realize or intend. Take back control in your browser.
Business & Finance | Business
Essential advice for securing your small startup | TechCrunch
Jeff Bezos’ phone was hacked. And if the richest person in the world is vulnerable, chances are good that your startup could get hacked, too. The good news is that, as a tiny company, you’re not a big target. But as soon as you hire your first employee, i
Science & Technology | Tech
How to secure your WhatsApp account from social hacking
It’s easy to secure your WhatsApp account with a six-digit PIN, so we’d suggest setting one up as soon as you get the chance. Then, if your SMS code ever falls into the wrong hands, they won’t be able to sign in to your account.
Science & Technology | TECH
Google finds Apple Safari anti-tracking feature actually enabled tracking
Apple's Intelligent Tracking Prevention technology posed risks to privacy and security, a research paper concluded.
Science & Technology | Technology
A Twitter Bug Could Use Your Phone Number to Expose Personal Details | Digital Trends
A security researcher has revealed that it's possible to find phone numbers and match them to Twitter usernames, a security flaw that could leave millions of people's accounts exposed. The researcher said he'd already found the phone numbers of several hi
Advice & Self-Help | Helpful Advice
Warning: Paying for Gas at the Pump Could Make You a Target for Hackers
Gas pump card readers are less secure, and now criminals are using a new phishing scheme to hack the devices and commit fraud.
Business & Finance | Business
US Finalizing Rules to Limit Sensitive Tech Exports to China, Others
WASHINGTON—The Trump administration is finalizing a set of narrow rules to limit exports of sophisticated technology to adversaries ...
Science & Technology | Tech
Why You Should Never Charge Your Phone in Public USB Ports Without a USB Data Blocker
Public USB ports could be an easy way for hackers to steal your device’s passwords and other important data.
Science & Technology | Technology
Millions of Twitter and Facebook users may have had their personal information compromised
Twitter and Facebook have confirmed millions of users' personal information may have been compromised by malicious software in third-party apps.
Science & Technology | Science & Technology
Macy's says its website leaked credit card info to hackers for a week
There's a chance sensitive info had been stolen for a full week.
Science & Technology | Tech News
SecurityWatch: After a Breach, Should You Still Trust Your VPN?
The recent breaches of NordVPN and TorGuard demonstrate how trust is an intangible but important feature of security software. If you lose confidence in a security product, such as a VPN, it's probably time to ditch it.
News | News
Amb. Dore Gold - American Withdrawal and the Future of Israeli Security
Amb. Dore Gold – American Withdrawal and the Future of Israeli Security This article originally appeared in The American Interest on October 16, 2019. Jerusalem Center for Public Affairs Near the close of Israel’s election campaign last month, Pri
Science & Technology | Tech
Scam Alert: New Phone Scam Uses a Real Text From Your Bank to Trick You | Mental Floss
If you get a call from someone claiming to be your bank, you should always be cautious. Here are some tactics one new phone scam uses to trick people.
Science & Technology | Social Media
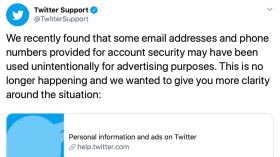
Twitter says it unintentionally misused user data for advertising
Users saw adds targeted based on email and phone numbers provided for security.
Science & Technology | Tech News
How malware uses web apps to turn PCs into conduits for attacks
It's not just botnets that can hijack PCs for nefarious ends. Microsoft and Cisco's Talos researchers have identified a new malware strain, Nodersok (or Diverg...
Miscellaneous | Interesting Links
Neighbors are using these smart cameras to track strangers' cars — and yours
Neighborhoods around Los Angeles are signing up for a new service: security cameras that automatically read the license plates of every car that drives by from a company called Flock Safety
Science & Technology | Tech
Google says iPhone security flaws let websites hack away for years
Malicious sites installed a "monitoring implant" that compromised personal data on iPhones that simply visited them, according to security researchers.
Science & Technology | Technology
That Apple Card may not be as private as you think
Apple's new credit card may not be as private as you think.
Miscellaneous | Interesting
Pentagon Gets Ernst’s ‘Squeal Award’ for Buying $30M of Risky Chinese Computers
WASHINGTON—Department of Defense (DOD) officials bought $30 million worth of computers and related equipment from Chinese companies last ...
Science & Technology | TECH
Bluetooth is bad and you should stop using it
Everyone uses Bluetooth. Perhaps they shouldn't.
Science & Technology | Tech
Making calls with Siri or Google could lead to you getting scammed
If you've ever used Siri or Google to call a business, you could be in danger of falling victim to a new scam the Better Business Bureau is warning.
Science & Technology | Israeli Innovation
Israeli Cybersecurity Firm Aims For More Secure Future By Eliminating Passwords
From hardware tokens to biometric methods, Israel's alternative authentication solutions are pushing weak passwords out of style. | NoCamels
Science & Technology | Tech
How to turn your old phone into a home security camera - CNET
This is how to give your outdated phone new life.
Science & Technology | Technology
The video game industry is a black hole for cybersecurity
Without a fundamental change in approach from both gamers and the industry overall, the magnitude of the security problem shows no signs of slowing down
Miscellaneous | Interesting Links
Safe Deposit Boxes Aren’t Safe
When Philip Poniz opened Box 105 at his local Wells Fargo, he discovered it was empty — and that he was totally unprotected by federal law.
Science & Technology | Technology
Read this before using FaceApp — you give up more personal data than you realize on this Russian-made app - MarketWatch
FaceApp has gone viral again with a feature that makes users look elderly, but experts say it may pose security concerns.
Science & Technology | Tech
Israeli company claims it can unlock any iPhone up to iOS 12.3 for police
Israel-based forensics firm Cellebrite claimed that its UFED Premium service can unlock iPhones and iPads up to iOS 12.3 and high-end Android smartphones such as the Samsung Galaxy S9. The device will be sold as an on-premises tool, which means that the p
Psychology | Psychology & Psychological Research
10 Amazing Benefits of Hugging—According to Science
Hugs are a powerful expression of trust and affection. They are also surprisingly impactful thanks to their effect ...
News | News
GAO Report: Travel Ban Rate Under Obama Was 16 Times Higher Than Trump - Sara A. Carter
Data analysis in a GAO Report shows that under President Obama the travel ban rate for security reasons was 20 times higher than under Trump.
Politics | Trump Politics
Blame Activists, Cartels for Crisis at Border, Not Trump
Trump is not one to stand by and not try every possible legal option to get the job done—and that includes shaking up the team.
Business & Finance | Business & Finance
6 things small businesses can do to improve cybersecurity
NEW YORK (AP) — Small businesses can be more vulnerable to cyberattacks than larger companies because they often don't have sophisticated and comprehensive systems to protect themselves from...
Miscellaneous | Interesting
CEO Offers to Build 234 Miles of Border Wall for $1.4 Billion
A builder from North Dakota is offering to put up 234 miles of border walls on the U.S.-Mexico border for $1.4 billion
Science & Technology | Social Media
Some major Android apps are still sending data directly to Facebook - The Verge
Major Android mobile apps from companies including Yelp and Duolingo send data to Facebook immediately after a user logs in, according to a new report from the London-based UK charity and watchdog group Privacy International (PI). This data transfer happe
Science & Technology | Tech
Apple left another big macOS security hole open for 90 days, Google says
Apple's memory management system is too trusting of previously mounted disk images, according to Google researchers, leading to a dangerous vulnerability.
Science & Technology | Technology
New flaws in 4G, 5G allow attackers to intercept calls and track phone locations | TechCrunch
TechCrunch - Reporting on the business of technology, startups, venture capital funding, and Silicon Valley
News | News
Life Near Texas Border: Mother Fears for Kids’ Lives
RIO GRANDE CITY, Texas—Martina Arredondo sleeps with a gun. So far, she has killed a few rattlesnakes with ...
Miscellaneous | Interesting
Cutting Government Waste Could Provide Border Wall Funding, Meadows Says
Rep. Mark Meadows, R-NC, floated a compromise solution on Jan. 15 to end the nearly one-month long partial government shutdown hinging on a funding impasse for a barrier wall on the U.S. southern border.
News | News
Trump Sets Goal of Missile Detection ‘Anywhere, Any Time, Any Place’
WASHINGTON—President Donald Trump announced the release of the 2019 Missile Defense Review on Jan. 17, while Pentagon officials ...
Politics | Trump Politics
The Men and Women Standing on the Frontlines Know: We Need a Wall
Politicians in Washington seem to think the fight over border security is just another political football to play ...
News | News
Local Resident Rips Apart Acosta's Border Wall Claim With His Own Photos
Acosta inadvertently proved that border security actually works.
News | News
US Border Patrol Reports 300% Increase Of Border Violence, Illegal Immigrants Assaulting Agents
The Border Patrol reports that assaults against its agents have spiked, but Democrats still think we don't need a wall on the US-Mexico border.
Miscellaneous | Interesting & Helpful Information
Low Self-Control When for Online Sales Relates to High Risk For Cybercrime
If you've got low self-control, there's a good chance you'll fall victim to cybercrime, a recent study out of Michigan State University finds.
Politics | Politics
EDITORIAL: Time to finish the Wall
If President Trump sends a wish list to the North Pole, it might say something like this (and he had better hurry): “All I want for Christmas is a big, beautiful wall.” If congressional Democrats send a letter, it would be addressed to the Gri
News | News
Tijuana Mayor Blasts 'Horde' of Caravan Migrants, Demands Immediate Action
'You’re going to tell me we have to respect human rights,' he said. 'But human rights are for law-abiding humans.'
News | National News
Presidential Proclamation Addressing Mass Migration Through the Southern Border of the United States | The White House
The United States expects the arrival at the border between the United States and Mexico (southern border) of a substantial number of aliens primarily from Central America who appear to have no lawful basis for admission into our country. They are trav
News | News
General in Charge of Border Response Warns This Migrant Caravan Is 'Different'
'I firmly believe that border security is national security.'
Science & Technology | Tech
Yikes! Online phishing attacks up 297% over last year
An online investigation revealed that phishing attacks are up 297 percent. Scammers using social media and online retailers to get access information
Politics | Politics
Reporter Proves Trump 100% Right, Officials ID Overseas Nationals Lurking in Caravan
Trump's time to act is now.
News | News
BREAKING: Hillary Clinton Loses Security Clearance Amid Email Scandal
Hillary Clinton lost her security clearance according to an announcement from the Senate Judiciary Committee on Friday. Senate Judiciary Chairman Chuck Grassley revealed that Hillary Clinton’s aide (who magically became her lawyer) Cheryl Mills alon
Science & Technology | Tech
Dozens of iPhone Apps 'Constantly' Sending Location Data to Data Monetization Firms
Dozens of popular iPhone apps are sharing the location data of millions of mobile devices with third-party data monetization firms, according to a...
Politics | Politics
This European country makes US look lenient on immigration | HeraldNet.com
Lawyers risk jail time if they even help a client fill out a complicated Hungarian-language form.
Science & Technology | Technology
1Password rolls out its biggest Mac update in years
AgileBits has finally released 1Password 7 for Mac, and it's the password manager's first major upgrade for the platform in years. The developer has made sure i...
Science & Technology | Technology
Chinese government admits collection of deleted WeChat messages
Chinese authorities revealed over the weekend that they have the capability of retrieving deleted messages from the almost universally used WeChat app. The admission doesn't come as a surprise to many, but it's rare for this type of questionable
Miscellaneous | Interesting & Helpful Information
The Unexpected Word That Shows Up on Every Hacked-Password List
Test your knowledge with amazing and interesting facts, trivia, quizzes, and brain teaser games on MentalFloss.com.
Science & Technology | Technology
Researcher estimates GrayKey can unlock 6-digit iPhone passcode in 11 hours, here's how to protect yourself
New estimates from a security researcher suggest GrayKey, a digital forensics tool in active use by U.S. law enforcement agencies, is capable of cracking Apple's standard six-digit iPhone passcode in an average of 11 hours. Longer codes, however, could ta
Science & Technology | Technology
This new privacy tool would speed up your internet, too
It's no joke how much data your internet service provider can collect about you. A new service from Cloudflare aims to change that.
Science & Technology | Technology
Android malware found inside seemingly innocent QR code apps
Google is getting better at keeping Android malware out of the Play Store, and that's leading attackers to use more sophisticated disguises for their rogue apps...
Science & Technology | Technology
Apple addresses iOS source code leak, says it appears to be tied to three-year-old software
Earlier this week, iOS source code showed up on GitHub, raising concerns that hackers could find a way to comb the material for vulnerabilities. The material is gone now, courtesy of a DMCA notice Apple sent to GitHub, but the occurrence was certainly not
Science & Technology | Technology
Securing Your Home Network
Why secure your home router? Home routers are directly accessible from the Internet, are easily discoverable, are usually continuously powered-on, and are frequently vulnerable because of their default configuration. These characteristics offer an intrude
Science & Technology | Technology
It’s time for the internet to block fake emails
One of the biggest upsides of the internet is that people from all over the world now have access to virtually anyone anywhere. Everyone is just an email..
Science & Technology | Computer & Coding Tips
Here’s what you can do to protect yourself from the KRACK WiFi vulnerability
Security researcher Mathy Vanhoef shared a serious vulnerability in the WPA2 encryption protocol.
News | Israel & The Jewish Community
How Israel Caught Russian Hackers Scouring the World for U.S. Secrets - The New York Times
Exploiting the popular Kaspersky antivirus software, Russian hackers searched millions of computers for American intelligence keywords. Israeli intelligence tipped off American officials.
Science & Technology | Technology
And to My Executor, I Leave My Passwords | Fifth Third Bank LegacyLink
What would the consequences be if, after your death, no one could access information you stored electronically? Use these tips to include and protect your digital assets.
Science & Technology | Technology
Banks Deploy AI to Cut Off Terrorists’ Funding
Computers are better than humans are recognizing small patterns.
Science & Technology | Tech
How a U.S. team uses Facebook, guerrilla marketing to peel off potential ISIS recruits - The Washington Post
With advertising dollars and big data, a tiny U.S. agency seeks to chip away at the militant groups’ online appeal.
Science & Technology | Technology
U.S. Intelligence Got the Wrong Cyber Bear
The U.S. government's technical report on Russian hacking identifies a tool that is readily available.
Advice & Self-Help | Advice
5 Tips for Keeping Your Home Safe While You're Gone for the Holidays
If you have travel plans for the holidays, you’re not alone. The stretch between Thanksgiving and New Year’s is one of the busiest long-distance travel periods of the year, according to the Department of Transportation. “Although July and August are the peak months for break-ins, nearly 400,000 burglaries occur in the U.S. during November and December,” says Sarah Brown, a home security expert.
Science & Technology | Technology
This USB stick is basically directly out of a sci-fi movie and we're scared
Why does a USB seem threatening? Well, this little piece of technology will completely destroy your computer once it's plugged into it.
Miscellaneous | NEW YORK CITY
15 Years After 9/11, Is America Any Safer?
The United States has spent $1 trillion to defend against al-Qaeda and ISIL, dirty bombs and lone wolves, bioterror and cyberterror. Has it worked?
Miscellaneous | Interesting Links
Why You Should Update Your iPhone Immediately
Especially if you have something to hide.
Science & Technology | Computer & Coding Tips
Tech Tip: Finding and Changing Your MAC Address in OS X
Every network card in your Mac, whether it's for Ethernet, Wi-Fi, or even Thunderbolt, has been assigned a unique identifier called a Media Access Control or
Politics | POLITICS
50 G.O.P. Officials Warn Donald Trump Would Put Nation’s Security ‘at Risk’ - NYTimes.com
Fifty of the nation’s most senior Republican national security officials, many of them former top aides or cabinet members for President George W. Bush, have signed a letter declaring that Donald J. Trump “lacks the character, values and experience” to be president and “would put at risk our country’s national security and well-being.”
Science & Technology | Computer & Coding Tips
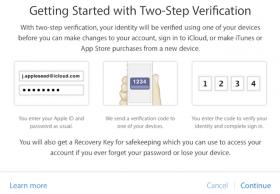
Two-Factor Authentication for Apple ID
Enabling two-factor authentication for your Apple ID is probably the most effective way to keep your Apple products secure.
News | That's News to Me
Emails: Key security features disabled on Clinton's server
News, email and search are just the beginning. Discover more every day. Find your yodel.
Politics | Politics
This is how the FBI destroys Hillary: The 10 questions that could end her White House dreams
These questions, if answered honestly, would most likely hand the Democratic nomination to Bernie Sanders
Science & Technology | Technology
Apparently there's ANOTHER hidden message inbox on Facebook
We're about to share with you something that will change your life, probably (and suck up any free time you have). There is a whole vault of unseen Faceboo
Science & Technology | Tech
Apple: New Malware Infects iOS Devices - Fortune
Palo Alto Networks researchers discovered new malware that can infect Apple iOS devices even if they aren’t jailbroken.
News | Interesting Links
A Stranger Is Following Her Closely, But When She Turns Around? This Is Going To Save A Lot Of Lives | facebook
9-1-1. Those three numbers have stood as a symbol of safety in the face of emergency for nearly 50 years. It's the first telephone number that ... | facebook
Science & Technology | Technology
This company hacked an iPhone with Play-Doh
If you’re protecting your smartphone with your fingerprint, beware strangers bearing Play-Doh.
Science & Technology | Technology
NSA chief: ‘Paris would not have happened’ without encrypted apps
National Security Agency Director Adm. Michael Rogers warns that encryption is making it “much more difficult” for the agency to intercept the communications of terrorist groups like the Islamic State, citing November’s Paris attacks as a case where
Family & Parenting | Kids
10 million California student records about to be released to attorneys - San Jose Mercury News
In a massive data release, California public-school records on about 10 million students -- including their Social Security numbers -- are about to be handed over to attorneys for a group suing the state, with both parties blaming the other for the impend
News | News
Frontier flight attendant gives list of armed passengers to customer
A man traveling on a flight from Chicago to Phoenix this past Sunday got a note from a flight attendant. She thought he was a Federal Air Marshal, and she told him there were two armed passengers on the flight.
Science & Technology | Technology
Don’t Be Hacker Bait: Do This One-Hour Security Drill
Do this one-hour digital security checklist to boost your data privacy and protect all your devices from hackers.
News | News
San Bernardino Shooter Passed DHS Counterterrorism Screening
CBS News reports that one of the shooting suspects in the San Bernardino massacre Wednesday passed the Department of Homeland Security's "counterterrorism screening as part of her vetting" for a visa. Writes the National Review:
Politics | Politics
House passes bill that could limit Syrian refugees - CNNPolitics.com
The House easily passed a bill Thursday that would suspend the program allowing Syrian and Iraqi refugees into the U.S. until key national security agencies certify they don't pose a security risk.
Science & Technology | Tech
Turn your old phone into a home security camera you can watch from anywhere - CNET
If you have one or more old phones laying around, here's a way to turn them into security cameras you can log into from anywhere.
Science & Technology | Tech
How to listen to (and delete) everything you've ever said to Google | Technology | The Guardian
Whether you’re asking directions or drunkenly swearing, Google never forgets, recording everything you’ve ever said to it. Do you dare listen back?
Science & Technology | Social Media
Don't believe that privacy hoax all over your Facebook feed
Sound the alarms: Facebook is about to start charging a monthly fee to keep your data private! It's all over your News Feed, so it must be true!
Politics | Trump Politics
Hillary Clinton's defense of her personal email server just got a little weaker
Democratic presidential front-runner Hillary...
Science & Technology | Tech
Hey Siri, you freak me out | VentureBeat | Security | by Sindy Nanclares
When Apple introduced the Macintosh, it promised 1984 wouldn’t be like Nineteen Eighty-Four. And yet there’s something seriously Orwellian about Apple in the year 2015.
Science & Technology | Computer & Coding Tips
Firefox users, here's a security flaw you'll need to fix
This bug can upload files from your computer if you visit the wrong news site. But you can close up the hole by downloading the latest version of the browser.
Science & Technology | Tech
Switching from Android to iPhone is makes more sense than ever - Business Insider
The latest Android malware is proof that iOS is more secure.
Politics | Politics
Intelligence officials: Hillary's private server contained information from 5 US spy agencies
Classified emails that were stored on the private email server of former Secretary of State...
Science & Technology | Tech
1975 Article On Internet Spying Not Written By Time Traveler, Probably
People often think about internet spying as relatively new. But the internet was used for spying before we even called it the internet—and when we look back at news articles from the era, we can’t say we weren’t warned.
Science & Technology | Technology
Hacking Tools: PITA uses radio waves to steal encryption keys | BGR
Just when you thought you were safe, a new hacking toy comes along and rocks your world. Imagine a tool exists that lets hackers pluck encryption keys from your laptop right out of the air. You can't stop it by connecting to protected Wi-Fi networks or e
Politics | From CNN
U.S. law enforcement thwarted plots timed to July 4th - CNNPolitics.com
With this use of social media recruits have a "devil in their pocket all day long that says 'Kill, kill, kill,'" FBI Director James Comey said.
News | News
My Way News - US: More than 21 million affected by new government data breach
WASHINGTON (AP) — Hackers stole Social Security numbers, health histories and other highly sensitive data from more than 21 million people, the Obama administration said Thursday, acknowledging that the breach of U.S. government computer systems was far more severe than previously disclosed.
News | That's News to Me
22 Million Affected by OPM Hack, Officials Say - Yahoo News
From Yahoo News: The U.S. agency burglarized by suspected Chinese hackers has completed its long-awaited damage assessment: In total, more than 22 million people inside and outside government likely had their personal information stolen, officials announc
Business & Finance | Business
VCs and startups are now paying attention to a vital thing they used to ignore
If a startup wants to get noticed, there's one new important thing they must pay attention to: How secure they are.
Science & Technology | Technology
The real story of how the Internet became so vulnerable
Scientists worried about intruders and military threats, but they didn’t anticipate that the network’s users would attack one another.
Science & Technology | Technology
Solid-state drives lose data if left without power for just a few days | ZDNet
Solid-state drives are great for performance, but data security must come first.
Science & Technology | Technology
5 simple internet safety tips from one of Google's information security engineers
These are so simple that everyone should be following them.
Business & Finance | Business
RadioShack Bankruptcy Auction May Include Customer Data - Fortune
More than 13 million e-mail addresses and 65 million customers' names and addresses are included in the RadioShack bankruptcy auctions.
Science & Technology | Technology
Google security temporarily compromised by fake digital certificates | VentureBeat | Security | by Dylan Tweney
Bad news for Google — and for anyone who uses its products: The company revealed today that it has discovered several fake digital certificates for some of its domains.
Science & Technology | Computer & Coding Tips
How to See If Your VPN Is Leaking Your IP Address (and How to Stop It)
VPNs are great for security, but one of the big reasons many people use one is to mask or change their IP address. This lets you get around location-based restrictions on content, or check if your provider is throttling your connection. Unfortunately, a n
Science & Technology | Computer & Coding Tips
OS X Yosemite update tackles 'surprise' Mac security flaws
You know those unpatched Mac security exploits that Google revealed a few days ago? You probably won't have to worry about them any more. Apple has relea
Science & Technology | Computer & Coding Tips
Watching a USB Hack in Action Makes Me Never Want to Leave My Computer
Remember BadUSB, the pervasive and unfixable security vulnerability that turns every USB device into a vector for attacks against just about every computer? The one that's out in the wild now? I always knew it was bad, but this video really brought it hom
Science & Technology | Security
Smooth Surface SAML Single Sign-On -
Under the surface, SAML Single Sign-on's webbed feet are paddling like crazy to complete the SAML algorithm that performs secure and seamless transitions
Science & Technology | Science & Technology
Pack Those Authentication Fears Away: Authentication -
Certain 2FA solutions help make the transition to stronger authentication easy. PortalGuard’s Crossroads tech brief, Navigating the Authentication Crossroad